Today, everything seems to be at our fingertips. The internet brings a wealth of information, entertainment, and products to our door on demand. You can take classes from world renowned experts and start new businesses with a series of keystrokes. The web has also become a tool of social change. Crowdfunding sites such as Global Giving help charitable missions receive donations from ordinary individuals. Social media was a key coordinating space for the Arab Spring in 2011, as well as being central to more recent movements like #MeToo and Black Lives Matter.
…we need to look to cyberspace as a global commons, with clearly understood rules to ensure everyone has free and equal access to the opportunities of the World Wide Web.
While one can debate the long-term impact of these movements, the internet was a key component of their success in organizing and sustaining their drives for change. The massive degree of connectivity provided by the World Wide Web can be the cornerstone for progress, but it can also be its Achilles’ heel. In countries where the government has some degree of control of access to the internet, such as China or Egypt, leaders can restrict what data their citizens can access or even completely block out internet access. Such regimes can also track users’ behaviour online in order to reinforce their surveillance state. Facial recognition and other identifying technologies can harvest and sort massive amounts of data in order to allow oppressive regimes to pick out key organisers and single them out for persecution. As more advanced technologies come into play, the power of states to monitor and control their populations increases as well. As cyberspace becomes an increasingly important space for global interaction, we need to look to cyberspace as a global commons, with clearly understood rules to ensure everyone has free and equal access to the opportunities of the World Wide Web.
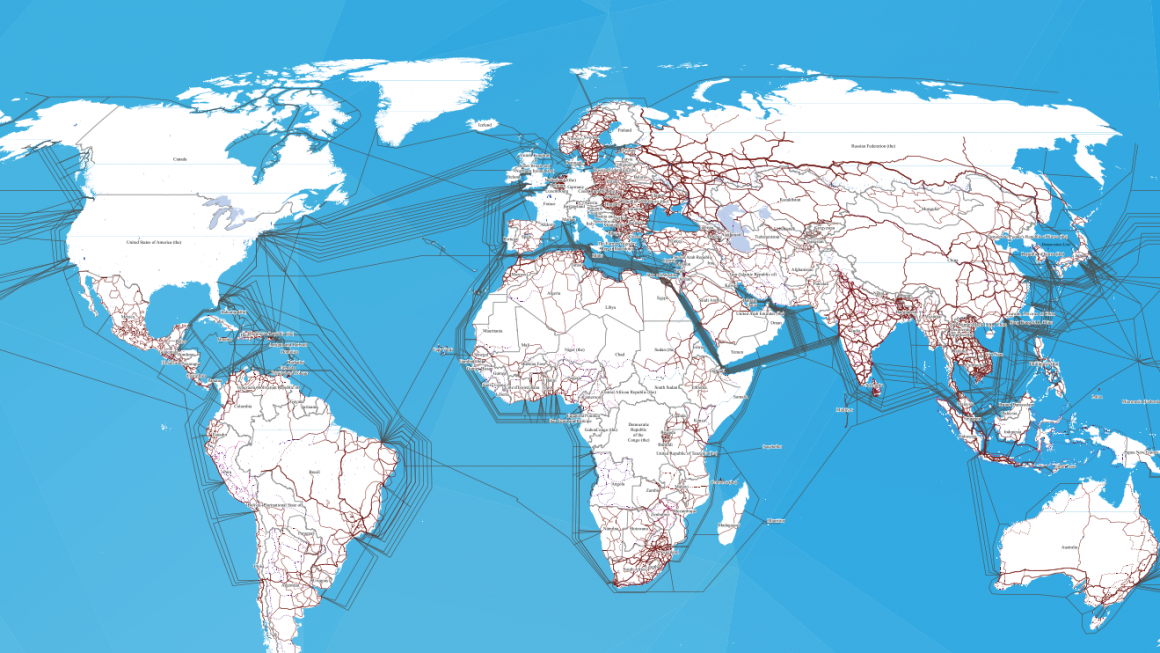
Cyberspace is usually thought of as an abstract concept used to discuss the ethereal web of interconnected data that is accessible through one’s web browser. It is everywhere and nowhere, so it is hard to conceptualize anyone “controlling” the internet. However, there is a very tangible web of cables and servers that make up the physical infrastructure needed to store and transmit that data. The point where one taps into this network is called an access point. For individuals, this normally represents their router or other such equipment that connects devices to the internet. Controlling each individual access point would be next to impossible for any government wishing to restrict its citizens’ use of the internet. Instead, states target locations where communication comes to a bottleneck.
These bottlenecks naturally occur where select, larger cables enter a national territory, whether coming ashore from the web of undersea cables or moving overland from a neighboring country. These points are under the control of the state whose territory they fall within, though for the actual function of the internet this fact is irrelevant. Individual segments of data choose the fastest path from their origin to their destination, regardless of what borders it ends up crossing to reach the user. Normally, this would make regulating internet traffic impossible, as monitoring all possible pathways the data could take would be prohibitively difficult.
To ensure control, countries like China have simply ensured that all of the access points available to their citizens are controlled by the government. By controlling these information pathways, these governments can serve as gatekeepers, curtailing access to certain information or even completely shutting down their citizens’ access to the global network. There are a wide variety of technologies that can perform the individual censorship tasks, but it is this overarching control of data lanes that allows for their complete implementation.
If data can only move through state approved channels, then it is much simpler for governments to sift out undesirable data and prevent it from reaching their citizens. Additionally, this control allows these states to pressure tech companies to conform to national regulations regarding censorship and technology sharing by holding the company’s access to the domestic population hostage. In coordination with domestic legislation, the control over access to one of the world’s largest economies helps China force private companies to participate in their censorship regime.
Individuals should be free to utilize the mix of public and private goods provided through this technology to engage in business, express political views, and engage in the broader human experience. The ability for nations to selectively censor both their own citizens and the global community runs contrary to this idea of the internet as a global commons.
To resolve this issue, it is necessary to bring at least some international control to the internet’s physical infrastructure. The most obvious would be to establish the access points as autonomous zones administered by an agency such as the United Nations, similar to the status of the UN Headquarters territory in New York. However, it is incredibly unlikely that nations would be willing to surrender portions of their national territory for such a purpose.
More realistic is the implementation of a set of international standards for how these larger access points should be managed. These standards could be established and regulated through the International Telecommunication Union (ITU), focusing on ensuring that nations are not using these domestically controlled bottlenecks to host technologies geared towards censorship or that provide a killswitch that can shut off nationwide access to the internet. Such regulations will need to be backed by consequences for non-compliance, whether in the form of sanctions or some other form of political or economic reprisals.
By ensuring open passage of data through internationally regulated access points, the costs to maintain the current degree of censorship would increase substantially, as nations would be forced to try and control smaller internal junctures, which are significantly greater in number and territorial spread. While these regulations will not solve all of the issues threatening the independence of cyberspace as a global commons, they can serve as an achievable foundation on which to build.